We support all OIDC compliant identity providers. In the User Guides section, you can find selected configuration tutorials that explain how the settings look like on the provider side.
This reference, explains what you need to do in your Container Registry instance to enable and configure the OIDC login. Usually, you should proceed with this tutorial if you have access to your OIDC’s provider management console to set up new client.
Besides, make sure that you made yourself familiar with general notes on different authentication modes as each of them may have its advantages and disadvantages.
Switching the authentication mode from the database mode to OIDC is only possible on a system without existing users.
To resolve such issue, the system admin (admin) needs to delete all users manually in the UI or via API.
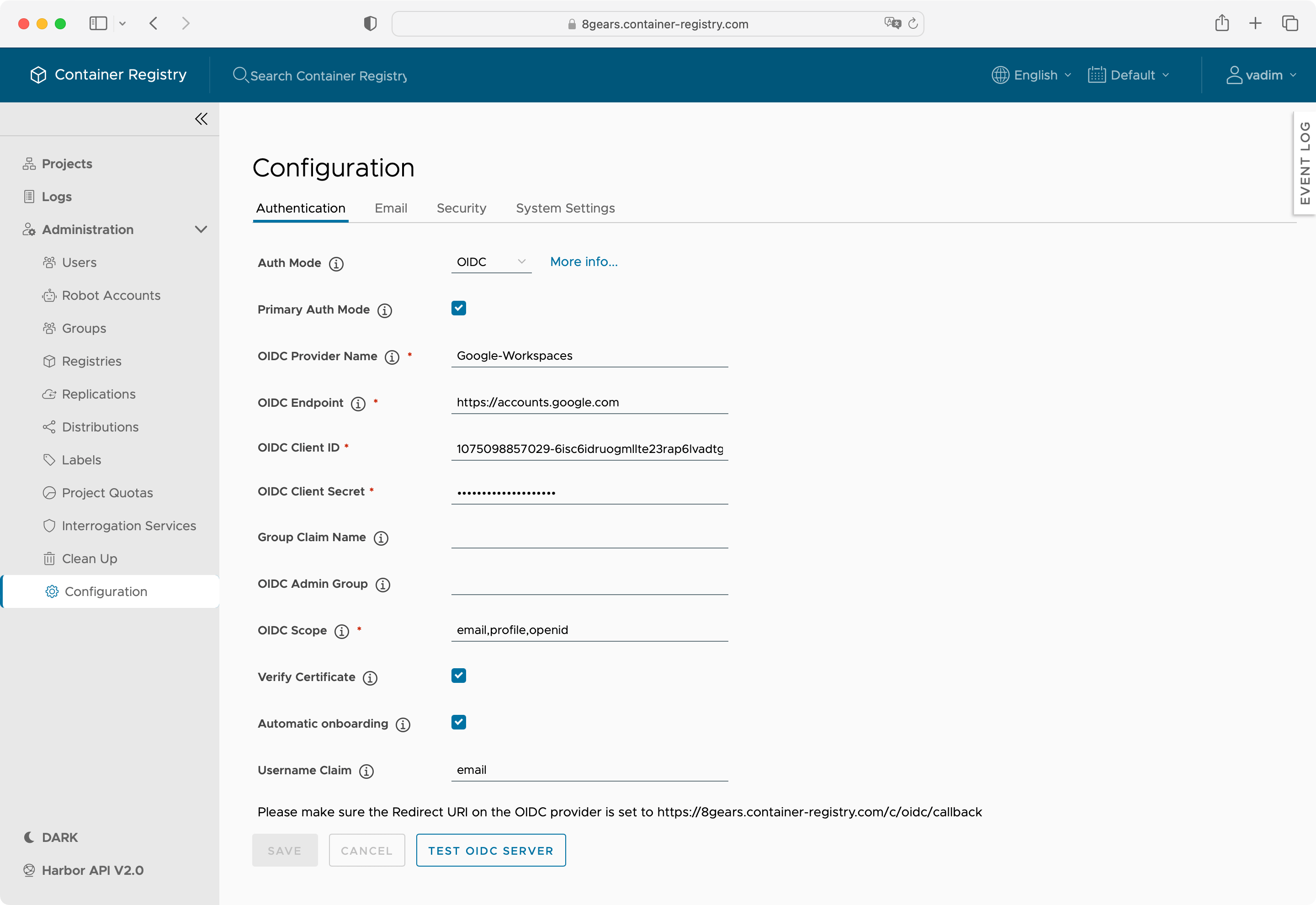
Primary Auth Mode
When enabled OIDC becomes the default way for users to login.
The login screen where the user can select to log in via the identity provider or via local DB will not be shown and redirect the user to the identity provider configured here.
Login via DB is still possible but the admin user need to visiting the url account/sign-in explicitly in order to be able to log in via username and password.
OIDC Provider Name
The OIDC Provider Name is for you to identify the selected IDP or the configuration. The name is not visible to the user.
OIDC Endpoint
Mandatory
Enter the OIDC Endpoint of the publicly accessible endpoint that serves its OpenID configuration document /.well-known/openid-configuration.
The URI of the configuration document’s endpoint is usually visible in the identity provider management console.
For some identity providers configurations an ending slash / is required.
OIDC Client ID
Mandatory
The client id is a public identifier for apps, given out by your identity provider, if you create a new App.
Fill in the field with information you copied from your identity provider.
OIDC Client Secret
Mandatory
The client secret is should only be known to the application and the authorization server. It is essential the application’s own password.
Fill in the field with information you copied from your identity provider.
Group Claim Name
Enter the Group Claim Name which contains the list of groups the user is member of in the ID Token.
During the login the user is added to the Harbor group he is member of.
OIDC Admin Group
Specify a name from the Group Claim Name, where users belonging to that group will have admin privileges.
OIDC Scope
Mandatory
In OIDC Scope, enter at least openid,email and offline_access. Optionally add profile to get users first and last name.
Verify Certificate
Tick on Verify Certificate if your provider offers a CA (Certificate Authority) Signed Certificate and not a self-signed one.
Automatic Onboarding
Specifies if users will have the option to define their own username when signing up for the first time.
If you select Automatic Onboarding, the username request dialog screen won’t be shown, and users will be automatically assigned their usernames as they appear in the OpenID token;
Username Claim
This setting only works in combination with Automatic Onboarding
If you activated Automatic Onboarding, you may also specify the property in the ID token that will be used as the usernames.
Test the connection to verify the configuration against the IDP. Hit Save if it worked out well.
When you log out and then log in again, a new Login via OIDC provider button will appear on the login screen. As a system admin, you can continue to use your old credentials and Username and Password field to access your instance.
Independently of your provider, you need to set a redirect URL, the is also displayed in the line above the Save Button.
https://your-instance-domain.com/c/oidc/callback
Users’ CLI secrets my not be valid after a some time. In OIDC enabled setups, the CLI secret depends on the validity of the JWT, which usually has a validity period defined by the identity provider.
In cases where the user’s CLI password isn’t working, the user must log in to the Container Registry UI to refresh the JWT.